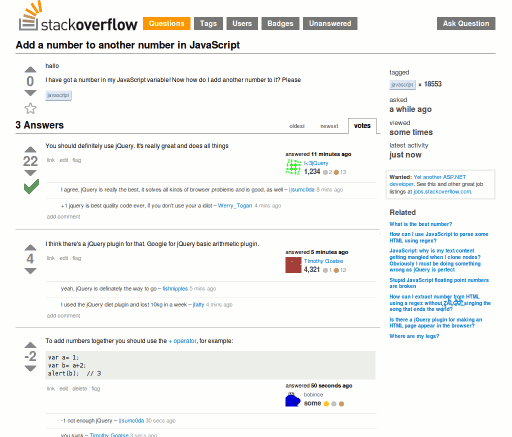
$('#mytable tr:not(#'+$(tr).attr('id')+'~tr)').size()-1
Clearly just saying tr.rowIndex is no good. It's too fast, or too readable, or something.
(Actually the real reason it's a no-go because it's part of the standard DOM, which
everyone knows is “full of [unspecified] browser bugs” which using jQuery magically manages to fix, except when
it doesn't.)
The Lure Of Strings is here once more. jQuery users want to work with strings, not DOM objects. Strings
are easy! You can make a selector string $('#'+id) so much more easily than
having to type out boring document.getElementById(id), and it'll only be a bit
slower, and it'll only fall over when there's a dot or colon in the ID, and that probably won't happen, unless
maybe it does, so that's OK.
Plus, you can make a div by saying $('<div>'+message+'</div>') instead of
having to muck around with document.createElement('div') and text nodes. Hooray!
Only... hang on. You've not escaped that HTML, and have probably just created a cross-site-scripting
security hole, only on the client side this time. And after you'd spent so long cleaning up your PHP to
use htmlspecialchars on the server-side, too. What a shame. Ah well, no-one really cares about correctness
or security, do they?
jQuery's not wholly to blame for this. After all, the innerHTML property has
been about for years, and already proved more popular than DOM. But the library certainly does encourage
that style of coding.
I do have some serious reservations about a lot of the stuff jQuery does, but that's a long, complicated
and boring tirade for another time. Preferably a time when I've got some actually-useful
JavaScript library stuff on my software page instead of the manky 8-year-old scripts aimed at IE5 and
Netscape bleedin' 4 which live there at the moment... but that would involve updating this site.
Which it turns out I'm really not very good at. Tsk, eh?
PS. I don't much like Prototype, either.
21st April 2009

Spyware: end of an era

That's it; “spyware” is done. Zango (né 180solutions), the last of the major spyware vendors,
is
no more.
It is unclear at this point what parts of Zango live on after being purchased by blinkx.
I suppose it's possible that it's a case of moving the system to new operators whilst shrugging off some of
the old debts. But whether blinkx have the means and intent to keep the adware network up and running or
not, it's the last nail in the coffin for the concept of adware. If 180, having swallowed up its other extant
competitors (Hotbar and CDT) can't make it work, the adware model is doomed.
And predictably so. It has always been blatantly obvious that adware does not offer an acceptable value proposition
for any rational customer: years of irritating ads and loss of control over your computer and privacy, in exchange for
some crappy smilies or video you can almost certainly get elsewhere for free? Not a goer. Even if you could be
persuaded to install it, the obvious course of action is to remove the adware again immediately afterwards.
So adware cannot be viable on legitimate terms. The only way to make it pay is to cheat: to hack
‘consent’ by hiding your agreement where no-one will see it; to target inexperienced or non-rational
customers who won't understand the agreement (in particular children); and to install without any
consent at all, through silent bundling or in the worst cases install by exploit.
180 and the rest of the industry did all of these; when finally threatened into curbing the
worst of this behaviour by legal threats and the FTC, they were no longer capable of keeping the
model afloat.
Ken Smith, previously CTO, offers a mixture of apologia and self-justification in
a
post-mortem at his blog. It's interesting to see how he views 180's actions, but
some of the comments seem a little disingenuous to me.
We partnered with some people that we should never have partnered with.
During that time period, my best estimate is that something like 4% of our installs during that time period
were completely silent, i.e., were the result of affiliates using browser security holes
I think this is a massive under-estimate. Perhaps only 4% of affiliates were directly
using browser security hole exploits themselves, but there were also many intermediary
affiliates that installed 180 software without any notice or consent, having themselves
previously been installed silently. For example, a 180 variant was installed by NeoToolbar,
which was itself installed by CoolWebSearch variants, which were installed by exploits. Another
was installed by MediaMotor (later shut
down by the FTC), which was installed by SmartBot exploits. And so on.
Plus there were many installs that were simple bundles rather than exploits, just with
no notification or consent that 180 software would be installed. I'd say this also counts
as silent; the figure must be much higher than 4% even ignoring the issue of whether
a few paragraphs of legalese in an enormous EULA squashed into a tiny scrollbox
counts as meaningful consent.
Empirically, I used to see 180 software all over the computers I was looking after, with
the owners unaware of what they had done (if anything) to receive it. But more
recently*, I've not come across a single one. Whilst some of that will have come from
greater customer awareness of the dangers of installing software with bundles attached,
the majority has to be up to the move away from silent installs.
(*: I'd say “since 180 cleaned up their act”
but that would imply their modern practices were completely clean. I don't
necessarily consider that the case. Some promotional materials are still misleading and/or
seemingly aimed at children, and much of the content used as bait by affiliates is worthless
at best — and at worst, as in the case of the fake torrents, illegal. But it is undeniable that
180's behaviour has been much better than in their heyday.)
Back in 2003, spyware meant "a program that your wife puts on your computer to track
what you're doing." By 2005, it was synonymous with "adware", which was an awkward
if reasonable description of Zango's business model. How did this happen?
Oh, that's an easy one. You get called spyware because your software spies.
180 software included long-term clickstream tracking functionality (which though not
immediately personally-identifiable can easily become so through leakage of information
in URLs), and, much worse, deliberate sniffing of e-mail addresses and personal registration
details from multiple third-party programs (eg. Outlook Express).
You may take offence because the primary purpose of the software is not spying, and demand
to be called adware instead as ads are the main thing the software is designed for. But your
software leaks information; security researchers have no way to verify what happens to that
information after it leaves the computer. If you don't want to be considered spyware, don't
spy. Don't do something incredibly suspicious like sniffing out the user's name, e-mail address
and ZIP code if you don't intend to use it.
(It's amusing how, over the years, “no spyware!” has become a phrase only ever used by spyware.
Like farts, where He Who Denied It Supplied It, “we're not spyware!” is an immediately obvious
red flag that something quite smelly is present.)
And very few of those programs had any sort of notice, QA, or presence in Add/Remove Programs:
in contrast, Zango had all of those things.
Only in the latter days. Earlier versions of Zango (originally ‘nCase’) were installed with no notice,
served unlabelled ads, occasionally crashed, and had no Add/Remove function; indeed, some
resisted being manually uninstalled. You had executables with completely random names, dropped
into different folders to be difficult to find. And when removed, many versions left an ActiveX
installer in-place, allowing nCase to be re-installed without any notice by any web site.
Malice or simple incompetence, there's no excuse for this stuff.
You're crying because your reputation was terrible in the later years of Zango despite having
improved things since the early days. But there should never have been any later years, because
the actions of the early days were simply unlawful. 180solutions's software
did untold damage to machines it had no authorisation to access; if the FTC or other
authorities had been more on the ball in 2002-2004 you would have been shut down already.
I'm working on another startup
I wish you luck — if it's a theology startup.
If it's adware again, not so much.
After all, they [the anti-spyware vendors] were in it to make a buck as well
No, not originally. The first wave of anti-spyware tools — OptOut, Ad-Aware and
Spybot Search and Destroy — were completely free.
They were originally written by amateurs to
satisfy the malware removal needs that were not being met by traditional anti-virus
vendors (who ignored the problem for years, perhaps afraid of litigious adware
companies like your own).
Anti-spyware in decline

Things are a bit different now of course. As described in
an earlier post, the category of adware barely exists any more. Instead we have the
annoying but relatively harmless bundled toolbars from Google, MS, Yahoo and Ask on one side,
with the trojans, botnets and fake anti-spyware apps installed by PPI fraud and Russian exploits on the other, not even
attempting to look legit. I guess if you're going to do exploits, the proper trojans pay better than adware.
There's very little in between (you still see the Mirar toolbar installed by the trojans occasionally,
but that's about it), so there's little left that the anti-virus people aren't already targeting. Generally
unsuccessfully targeting, but that's another
story. Some anti-spyware apps have themselves drifted out to target this more obvious
malware, with the result that there's little difference between them and the traditional anti-virus stack.
There is no longer really any place for dedicated anti-spyware.
But the anti-spyware companies now really are out to make a buck, and it's
hard to take a broken business model that's still making you money and just decide to pack it all in. This is leading to some
strange bedfellows. AVG and SpySweeper have been bundling variants of the Ask toolbar (previously
considered spyware), and now both
Ad-Aware and SpywareBlaster are pushing users towards TrialPay, one of those nasty schemes
where you have to sign up for dodgy offers you don't want, then cancel them and hope you don't have
to spend the next twelve months on a helpline trying to stop your credit card being billed. Which may not be spyware, but
it's certainly exactly the same kind of marketing unpleasantness that the adware companies loved to push. It's a
bit sad to see previously impeccable software teams go this way.
To be honest I don't even know why SpywareBlaster still exists; its ActiveX CLSID-based blocking was relevant
to the unsolicited commercial software threats of yesterday, but does absolutely nothing against the exploits,
trojans and rogue anti-spyware that dominate today. The parasite-detector script on this site worked in a similar
way, but has since been withdrawn as it's of almost no practical use any more.
(I'll probably remove the ‘parasite’ section itself completely soon. Certainly the advice about anti-spyware
software there is woefully out of date. Perhaps I'll replace it with an archive of the old, much-plagiarised
parasite list for historical interest.)
Plug out

Another point release of Firefox was released today, fixing more security holes. IE was a week ago with the
usual monthly round-up. It seems we've completely given up on the idea of having a secure browser, and
are happy to let it update once a month instead. It's a bit sad, but that's the price of having such a complex
and expanding feature set, I suppose.
But still, the majority of successful exploits recently aren't even targeting the browser, but plug-ins.
Quicktime, Real, Windows Media and especially Java have been targeted by the Russian malware gangs in
the past, but the current favourite by a mile is the Adobe Reader PDF plug-in.
Perhaps the reason these attacks are so successful is that while browsers are understood to be net-facing
software it is important to keep updated, users don't really understand what they have with plug-ins.
And why should they? If you install Adobe Reader, it says nothing about installing a PDF plugin. You wouldn't
naturally expect it to, because let's face it, no-one wants to read PDFs squished up in a little embedded box
in a web browser. It's an unpleasant experience even when it works, and it adds a whole load more
attack surface to the web browser. Plus it occasionally crashes.
Previously, to be attacked, you'd have to explicitly download and double-click
on a PDF you wanted to read. Now, you're at risk just by going to a web page. And not just known ‘dodgy’
web pages like porn and warez; any number of high-profile sites have been hacked, or included adverts
from networks that are hacked. For example for the last week, foxnews.com has been happily sending its readers
to PDF exploits. (Yeah, I know, Fox News is way dodgier than porn or warez ect ect jolly laughs and so on.)
When you install Microsoft Office, do you really want to be able to view Excel spreadsheets in your web browser?
That's what the installer quietly does for you. You'll probably never actually need that feature, but it does still make you
vulnerable to various Office Web Components exploits that have come out over the years. Now you have to worry
about keeping Office up-to-date.
When you install iTunes, do you expect arbitrary web pages to be able to
fire up the iTunes application? They can now, so if there are security holes in it you're at risk. You have to keep
it updated... that and the Quicktime plug-in it will also install behind your back. You can use the Apple
Software Updater to do it, but how can you trust that when it has been known to also bundle further unrequested
applications like Apple's Safari browser?