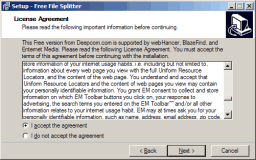
Don’t trust the EULA
Don’t trust the EULA
Just because the licence agreement seems clean, that’s no proof the
software isn’t going to stab you in the back anyway. You can opt out
of all the options there are, and still get hit by other parasites they ‘forgot’
to mention; some installers start loading parasites before even reaching the
EULA screen. A lot of parasitic software is installed without any notice whatsoever.
In many countries it remains untested whether ‘click-through’
licences have any legal weight at all anyway. (They are not a real contract, and it is
unclear whether simply running a program constitutes ‘copying’,
which would require some sort of licensing scheme under copyright law.)
 Avoid heavily-promoted free software
Avoid heavily-promoted free software
Think about it: if a company wants you to use their software so much that
they’re willing to spend money advertising it to you, they must get some
kind of gain out of doing so.
In some cases, the software might be a freebie to promote the company and
its other products. In many more cases, the software earns money by installing
parasites.
 Avoid junk software
Avoid junk software
Some of the most heavily-promoted software is trivial or pointless in nature,
aimed at users too inexpert to recognise this. Very often such software—worthless in
itself—is created solely as bait, to install the parasites that come with it.
For example: the many programs to correct the computer’s clock. Windows XP
already has this feature built-in and turned on by default; for other operating
systems there are a thousand other tiny programs to do it using the standard
internet NTP protocol, none of which feel the need to install parasites. (And anyway
correcting the small amount of drift in a modern computer’s hardware
clock by hand every six months is not really much of a hardship.) Yet adverts all
over the web are trying to convince you that your clock is probably wrong and
desperately needs fixing.
Other common examples include weather monitors, smiley icons, IM avatars
and mouse pointers, web form-filling and screensavers. Beware also ‘snake
oil’ products making technically questionable claims, such as software to
prevent crashes, increase memory size or network speed, or to speed up file-sharing
programs.
(Peer-to-peer file-sharing programs are themselves very often infested with large
quantities of the worst parasites—take care.)
 Prefer “Free Software” to “FREE DOWNLOAD!!”
Prefer “Free Software” to “FREE DOWNLOAD!!”
The Free Software and Open Source movements make the full source code of their
software available. This makes it difficult to hide undesirable behaviour such as spying
or advertising from its users. So Free and Open Source Software is generally more
likely to be free of parasites.
Ensure you download from the software’s official project site. Some parasite-laden
downloads have masqueraded as well-known open-source applications in the past, or
implied they were open-source without actually being so (eg. openwares.org).
 Be sceptical
Be sceptical
A company’s own assertion that their software contains “no spyware”
is next to worthless. Aside from the possibility that they are simply lying, there are many
ways the definition of spyware
can be twisted to exclude whichever parasites they want to install.
If you’re not sure, do some research. Do a search for the program’s name
together with ‘spyware’, ‘adware’ or ‘parasite’.
See what people are saying about it.
Browsing
In theory, browsing a web page should be safe; the web was deliberately designed not to
include active content. In practice however, poor security and user interface design
make web browsing potentially dangerous.
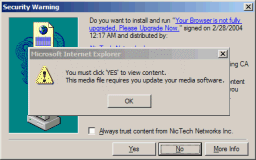
Installation through the web browser is the other major source of parasites, through
both ‘security hole exploit’ bugs that let software install automatically and
tricks that mislead the user into allowing a download they didn’t want.
 Refuse unrequested downloads
Refuse unrequested downloads


 Don’t just click ‘Next’
Don’t just click ‘Next’